While the importance of encryption and hashing cannot be underestimated, they are not a foolproof way to ensure that user passwords are impervious to cracking by a malicous actor. It is a security best practice to use a strong hashing algorithm which minimizes collisions for the storing of user passwords. Collions occur when two seperate strings result in the same hash after a hashing algorithm is applied. Weaker algorithms which produce a smaller hash digest are succectible to having collisions.
However, just using a strong hasing algorithm like sha256 alone may not be enough to protect against malicious actors cracking passwords if defenses are breached and stored password hashes are relased. This can be particularly true if the passwords used to generate the hashes did not have sufficient complexity rules applied to them when they were originally created.
This is largely due to something called rainbow tables. Rainbow tables are essentially a natural evolution from dictionary attacks. To create a rainbow table, an actor simply applies one of the well known and largely open source hashing algorithms to their list of common passwords in their dictionary. As hashing algorithms always produce the same digest when the same input is applied, the rainbow table becomes a hashed version of the dictionary used to crack the password.
One of the ways that systems can protect themselves from rainbow tables being used to compromise the passwords of their users is by employing the practice of “salting” passwords before applying the hashing algorithm. Salting is the addition of extra characters to a file before hashing it to ensure that the hash of the salted file is completely different than the hash of the original file.
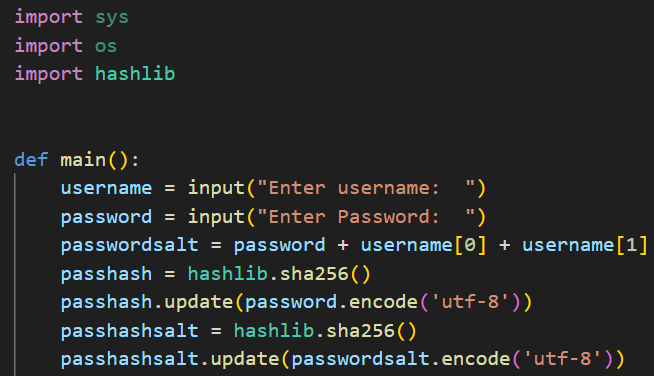
To demonstrate the effectiveness of salting, I created a small python program that takes in a username and password, and salts the password using the first two characters of the username. The program then hashes both the password and salted password using sha256. For the sake of the demonstration, this program does not employ data verification which would be neccessary in a production environment.
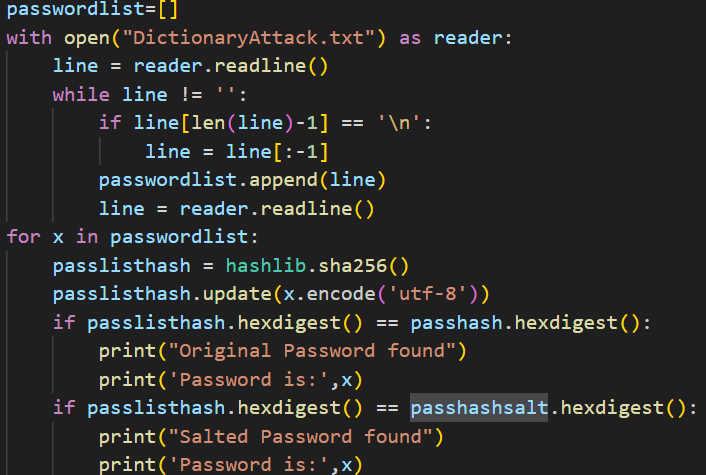
Next the program reads a dictionary attack text file and saves the common passwords as an array. The program then removes any newline characters, hashes the common passwords using sha256 and then compares the hashed common password versus the hashed user passwords and salted and hashed user password to determine if their is a match. The program simply prints out a quick message if any matches are found.
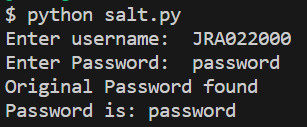
We can see from the demonstration that the dictionary attack was successful in identifying and displaying the original password, but the salted password is not seen as a match as the hash value is completely seperate from the hash of the original password.
I hope you found this quick post discussing and demonstrating the importance of salting to be interesting and informative.
Thanks,
JRArmstrong//
