Just as before, we will start our VM using the button on the top right of task 3. This will give us a few minutes to read the scenario. The scenario offers congratulations for stopping the inbound threat. Howver, we acknowledge that a threat may have already gained a foothold in the system and announce that outbound traffic will need to be reviewed. Our virtual assistant completes the scan and advises that there is suspicious outbound traffic which we will need to examine.
Just as before, we will need to open our terminal emulator and place snort into sniffer mode to obtain some packets to view. Like before, we will use the sudo snort -d command to allow us to review the packets. After the command has run for a little bit, such as 45 seconds, we can stop the service using Ctrl+c and review the packets for their information.
Looking at the header of the packet with significant information reveals good data regarding the protocol and ports involved in the outbound traffic. We can see several packets with significant data such as the following:
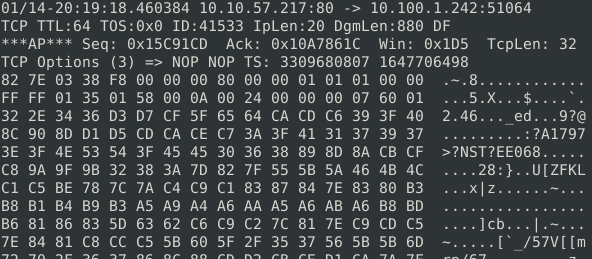
But the header of this shows it is utilizing port 80, which is used for http traffic. This in itself is not inherently dangerous. Perhaps we can continue looking at addational packets. The following packet does look suspicious, however:
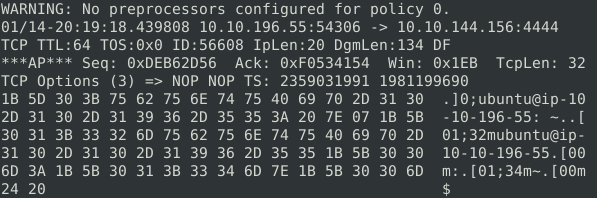
This packet is using a non-standard port, 4444, and appears to have the prompt for a bash shell: ubuntu@ip-10-10-196-55:. This definitely looks malicious and a good candidate for an external traffic block.
This gives us enough information to start writing a rule to block this traffic. Using the command: gedit /etc/snort/rules/local.rules we can write an outbound rule to block any traffic using port 4444 as we identified in the first step. We do not need to specify any content for this rule as we want to block all traffic leaving via this port. Our finished rule would look like: alert tcp any 4444 -> any any (msg: “Outbound traffic on port 4444”;sid: 2000005; rev: 1;)
Just as before, after we have saved and exited the edit window, we can check our rule using the configuration file with the-A Console modifer to ensure that the rule is alerting. The command to run is: sudo snort -c /etc/snort/snort.conf -A console . We can stop the service using Ctrl+c once we see successful alerts in the console window. Lastly, we can run snort in full IPS mode using the -A full modifer command as follows: sudo snort -c /etc/snort/snort.conf -A full . Once snort has blocked traffic for at least a minute, our flag.txt file will appear on the desktop.
We can now begin to answer our questions to complete the room.
Stop the attack and get the flag
Opening the flag.txt file reveals our flag.

What is the used protocol/port in the attack
Reviewing our packet from earlier we see that TCP was used on port 4444l
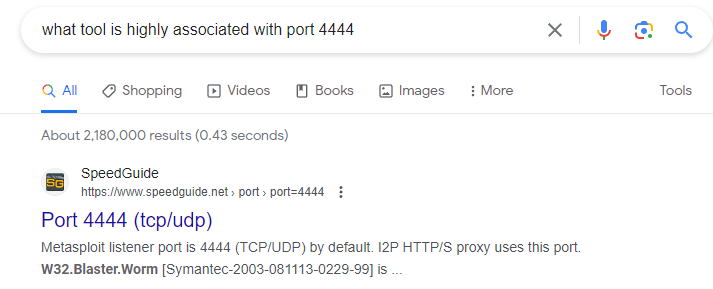
Which tool is highly associated with this specific port number?
As 4444 is not a standard port, google sarching for port 4444 will give us the best insight. As we can see, Metasploit is associated with port 4444.
The use of snort as an IDS and IPS can be tricky to learn and will undoubtedly require significant practice to become comfortable and proficient. However, there are several resources avialable on the web to help one become more comfortable with the use of snort. I hope you found this write-up to be concise, enjoyable, and most of all, informative.
Thanks,
JRArmstrong
