Carnage can be found at: https://tryhackme.com/room/c2carnage
Carnage is a blue team centric room on tryhackme focused on the use of wireshark for traffic analysis. As always, we start by joining the room and reading the scenario.
Task 1:
We can use the start machine button to begin spooling up our virtual machine. We can also begin by reading the scenario which describes a successful attack carried out through a malicious email which was opened and enabled by a member of the purchasing department. Our goal is to use the packet capture data to uncover malicious activities occuring in our network.
No answer needed.
Task 2:
We open wireshark on our virtual machine and then open the carnage.pcap file located in the analysis folder on the desktop.
Once loaded, we can start by filtering by the http traffic by seraching for http in the search bar. Immeadiately we see a GET request for a zip file which looks suspect. Double clicking on the frame brings up a second which where we can click on the arrow next to the frame number to gather information about the date and time of the packet. Clicking on the arrow next to Hypertext Transfer Protocol gives us information about the file which was downloaded as well as the site which hosts the file. We can now answer the first three questions from the room.
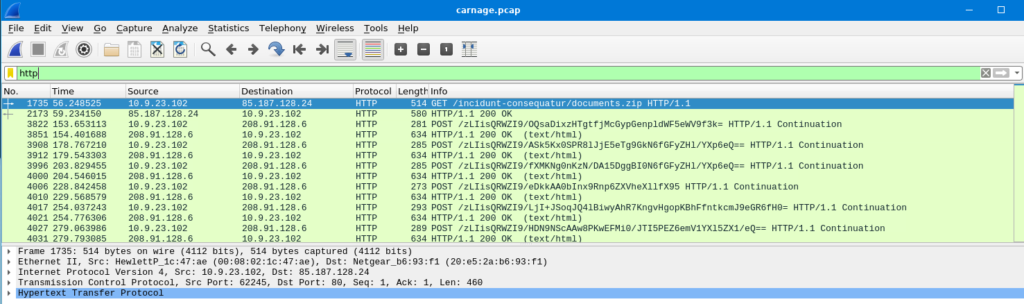
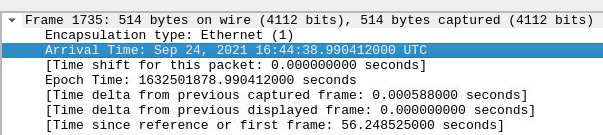
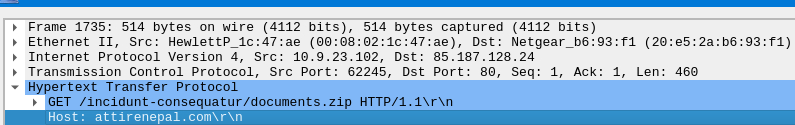
What was the date and time for the first HTTP connection to the malicious IP?
2021-09-24 16:44:38
What is the name of the zip file that was downloaded?
Documents.zip
What was the domain hosting the malicious zip file?
attirenepal.com
We exit this subwindow and right click on the packet to select follow-> TCP Stream to continue our investigation. After we scroll past the header, we find some important information regarding the server and file which was to be deloyed. We can find the name of the server as well as the scripting language and associated verision number for the server. If we look at the begining on the stream just past the secondary header, we can also see the name of the file within the zip file. We can now answer the next three questions.
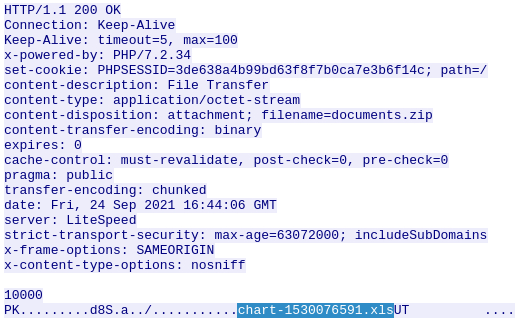
Without downloading the file, what is the name of the file in the zip file?
chart-1530076591.xls
What is the name of the webserver of the malcious IP from which the zip file was downloaded?
Litespeed
What is the version of the webserver from the previous question?
PHP/7.2.34
Looking foward at the next few questions, Carnage is hinting that we need to focus on three different malicious domains. Since we know this will likely be using HTTP and TLS as its encryption process we can narrow our results to just look at packets which start a TLS handshake starting at the time of infection and just shortly afterwards (per the hint) using this filter:
tls.handshake.type==1 and (frame.time >= “2021–09–24 16:45:11”) && (frame.time <= “2021–09–24 16:45:30”)
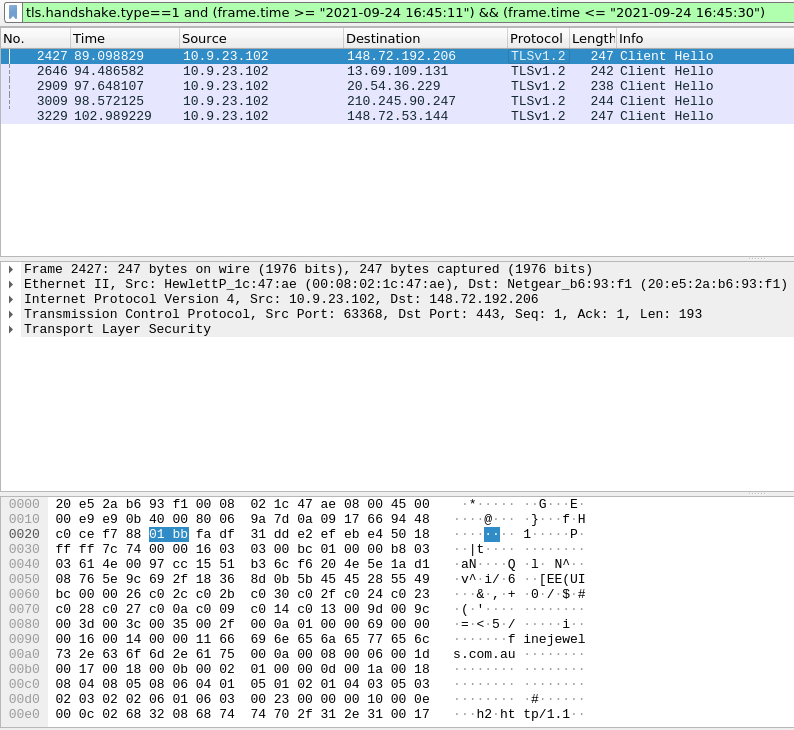
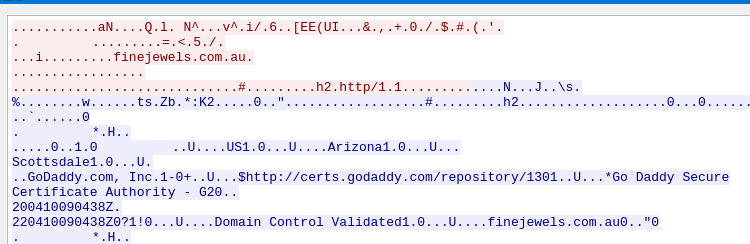
This reduces our results to just a few hits, and we can examine the packets individually to review their domains. A couple of the domains shown belong to microsoft, so we can likely exclude them from our list of malicious domains, or use virustotal to vertify their legitimacy. We can also gather additional information by following the TCP stream of the first domain. This allows us to view the cert issuer for that domain. We can now answer the next two questions.
Malicious files were downloaded to the victim host from multiple domains. What were the three domains involved in this activity?
inejewels.com.au, hietbiagt.com, new.americold.com
Which certificate authority issued the SSL certificate to the first domain from the previous question?
Godaddy
The next question wants use to find the IP adderss of the cobalt strike servers used for C2. Since it well documented that the use of GET and POST requests can help identify C2 beacons, we can filter our packet traffic to only show http requests using the filter ‘http.request.method==”GET”‘. This helps filter down our list down to 77 displayed packets, but we can use the Statistics-> Conversations window to show the various connections. C2 becons tend to use a lot of frequent connections, so by clicking on the TCP tab and sorting by ‘Address B’ we can scroll until we find a couple of IP address which have significantly more connections than other IP addressed.
We can then use virustotal.com to search the IP address we think are suspect. Clicking on the community tab shows we have found our two Cobalt Strike Servers as well as the host header information and server domain names. Doing this for both of our suspected malicious IPs allows us to answer the next four questions:
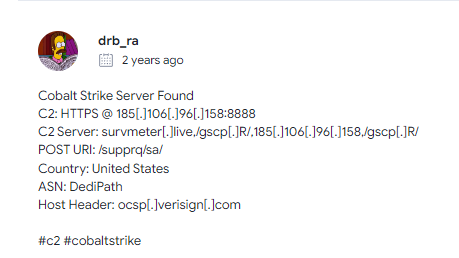
What are the two IP addresses of the Cobalt Strike servers?
185.125.204.174, 185.106.96.158
What is the Host header for thef irst Cobalt Stroke UP address from the previous question?
ocsp.verisign.com
What is the domain name for the first IP address of the Cobalt Strike server?
survmeter.live
What is the domain name of the second Cobalt Strike server IP?
securitybusinpuff.com