We can now start to look at POST traffic by changing our prevous filter to ‘http.request.method==”POST”‘. If we exam the first packet by clicking on the arrow next to Hypertext Transfer Protocol, we can find the name of the host where the post-infection traffic is being sent. Looking at the packet in detail in the bottom frame, we can also identify the first characters sent to the host after the POST/ header. Right clicking and choosing follow-> TCP stream allows us to view the entire communcation stream. We can now use that information to answer the next four questions.
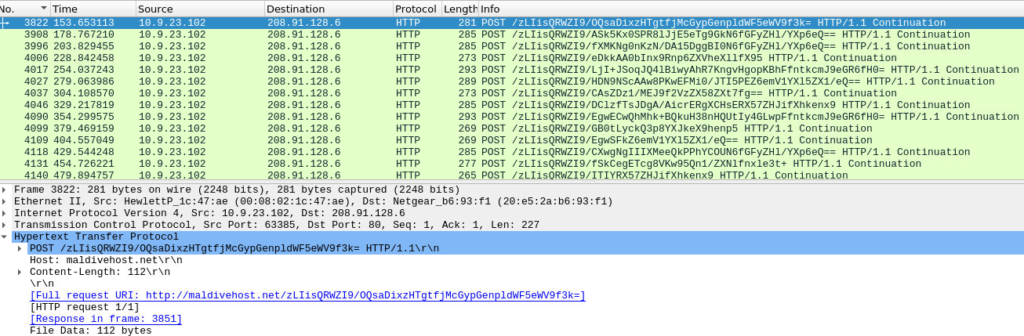
What is the domain name of the post-infection traffic?
Maldivehost.net
What are the first eleven Characters that the victim host send out to the malicious domain involved in the post-infection traffic?
zLIisQRWZI9
What was the length for the first packet sent out to the C2 server?
281
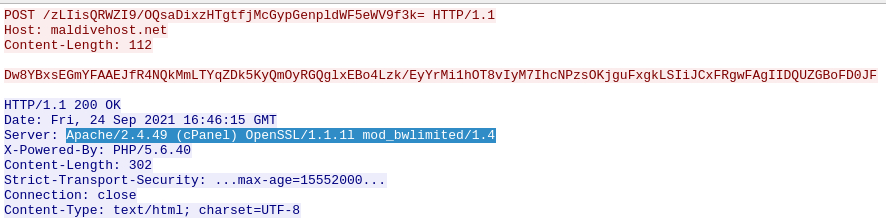
What was the Server header for the malicious domain from the previous question?
Apache/2.4.49 (cPanel) OpenSSL/1.1.1l mod_bwlimited/1.4
Our next question involves DNS requests using an API. We can filter for DNS frames involving an API using a quick filter of ‘dns && frame contains “api”‘ which significantly reduces our search results. We see some significant DNS responses happening after an original api request and response involving msn.com (which is likely benign.) Selecting the frame after the msn response and clicking on the arrow next to Frame allows us to answer the next two questions:
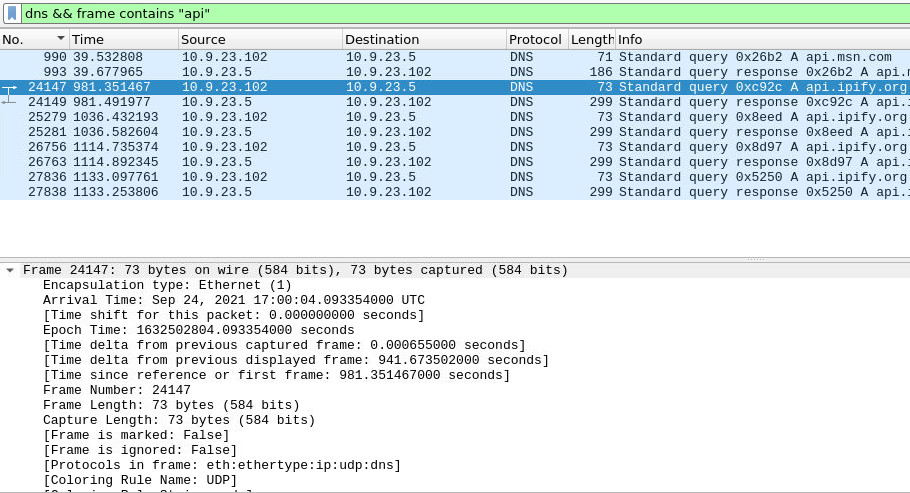
The malware used an API to check for the IP address of the victim’s machine. What was the date and time when the DNS query for the IP check domain occurred?
2021-09-24 17:00:04
What was the domain in the DNS query from the previous question?
api.ipify.org
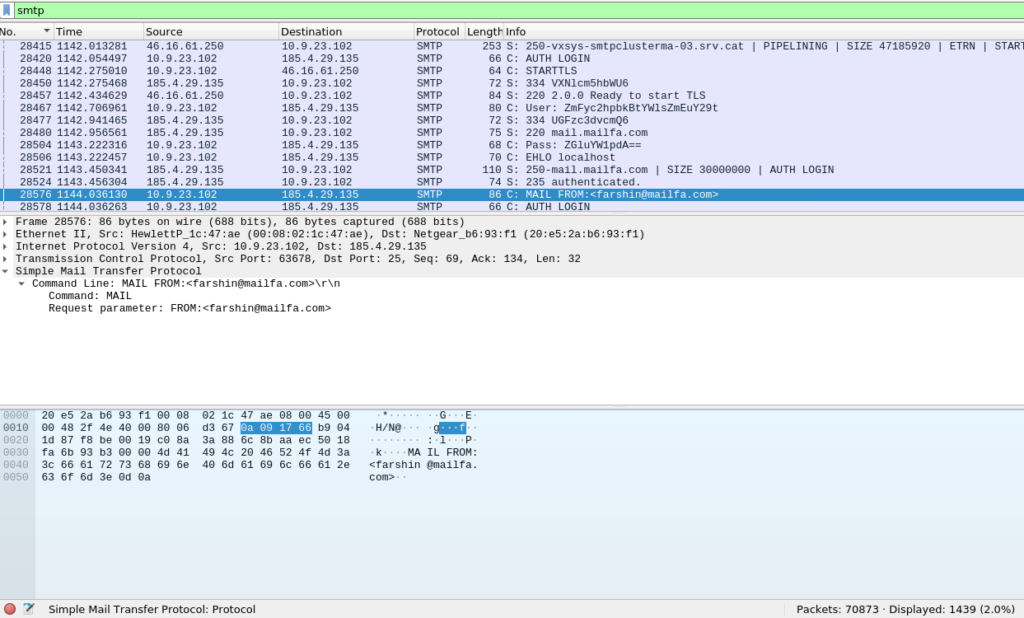
Our last two questions discuss SMTP traffic occuring as malspam. We can quickly identify frames which include the address of the sender by filtering using the search command: ‘frame contains “MAIL FROM” ‘. Lastly we can filter for all the SMTP packets by filtering by ‘smtp’. This allows us to answer the final two questions of the room.
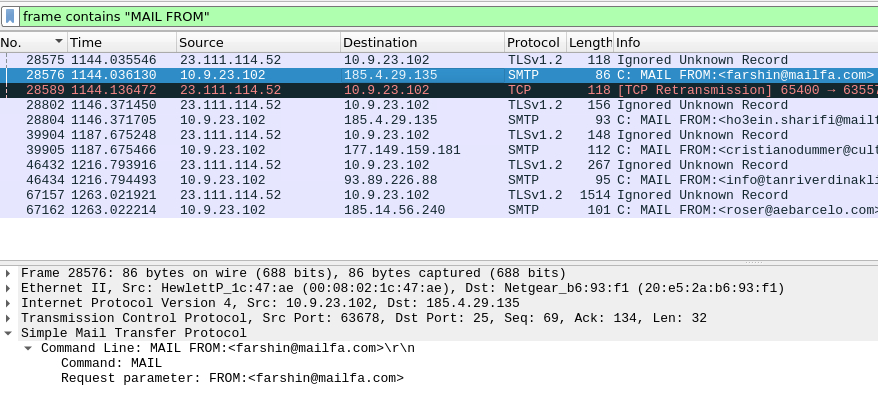
Looks like there was some malicious spam (malspam) activity going on. What was the first MAIL FROM address observed in the traffic?
farshin@mailfa.com
How many packets were observed for the SMTP traffic?
1439
Thank you again for your time, and I hope you found this walkthrough of the wireshark room, Carnage, to be informative and enterntaining and succinct.
Thanks,
JRArmstrong